Abstract
Free and Open Source Software (FOSS) components are the bedrock upon which our digital infrastructure is built. Most software — be it code that logs a user into their phone in the morning or checks the weather, to government systems that authenticate digital identity, streamline payments, and distribute health benefits — all use public code written by volunteer developers as part of their codebases. Code reuse is a common practice in software development where large software projects are made up of a collection of public projects so that developers and companies don’t reinvent the wheel every time they need to perform ancillary tasks. Despite the well-known practical benefits of code reuse and its prevalence in all the digital products and services that our society relies on, several security incidents in widely used FOSS projects have shown that such projects are often underfunded and under-maintained.
There are opportunities for targeted interventions in both technical and social aspects of OSS security. Policy solutions can help treat FOSS as the digital infrastructure that it is, by investing in maintaining critical software components used by the government and industry.
For software being created for government and public service initiatives like digital identity or welfare distribution platforms; efforts can be made to compel vendors to contribute to the maintenance of FOSS components they use, further strengthening the ecosystem they draw from. With the governments participating in and supporting the existing open source communities, they can contribute back to sustaining and nourishing an existing pool of expertise that is already passionate about the security and resilience of the software they create.
The Challenge
Background: What is Free and Open-Source Software?
Code reuse is a common practice in software development where large software projects rely heavily on existing public projects to implement their composite functionality. Most software — be it code that logs a user into their phone in the morning, reports the day’s weather, to government systems that authenticate digital identity, streamline payments, and distribute health benefits — all use public code written by volunteers as part of their codebases. This public code is known as Free and Open-Source Software (FOSS) or sometimes Free/Libre/ Open Source Software and refers to software that is freely available to anyone for consumption, modification and redistribution. (There are ideological differences in the use of each of the terms ‘free’, ‘open’ and ‘libre’ software. For the purposes of this paper we use the definition provided by Open Source Initiative[1])
It is this free sharing of code that makes most modern digital products work. Once a developer has solved a particular problem, such as encrypting data for secure transfer over the internet, they package the solution and make it available for other developers to use in other products under a permissible license. This enables other developers to use this package to encrypt their data without having to reinvent the wheel each time. This free and open sharing of coding languages, software libraries, components and projects enables the formation of companies that can use this existing digital infrastructure to build products and provide services to customers.
While the exact economic impact of FOSS is hard to measure because products are not required to disclose their FOSS usage, it is obvious that this digital infrastructure is both advantageous and necessary. Some industry estimates suggest 96% of codebases use open-source software as a building block[2],[3]. Github, one of the most popular platforms where open-source code is hosted, recorded over 413 million contributions to open-source software in 2022. Reports also show time and again that industry leaders and technical stakeholders prefer to increase the adoption of FOSS in their enterprise products because of lowered costs and perceived security benefits[4]. A 2021 report by the European Commission estimates the contribution of FOSS to Eurozone GDP to be between €65 and €95 million[5].
FOSS developers recognise the significance of their contributions. The top motivations to contribute to open-source software are not monetary, even for cases where developers are being paid by their companies to develop the software. Instead, developers like to be in a community with other like-minded people to solve challenging problems, build reputation, and learn new skills. Developers also believe in the mission of ‘free’ and ‘open’ software and have a deep commitment to their projects[6].
The FOSS Security Challenge
Open-source software is assumed to be more secure since, theoretically there are more eyes on the code and an active community which will catch defects better than any individual could. This may not always be the case. Several high-profile security incidents in widely used open-source software projects have drawn attention to the fact that such projects are often underfunded and under-maintained, meaning that maintainers are unable to catch security vulnerabilities or update components in a timely manner.
This can have severe consequences because the widespread use of open-source software means that a vulnerability in a software component or a library can have cascading impacts on all the tools that use it.
For example, in 2014 it was discovered that a popular open-source encryption library which is used by governments and technology companies around the world had a programming error that allowed hackers to intercept confidential data. The bug, called Heartbleed, affected almost half a million websites online given that it was a trusted, widely used software library[7]. There has also recently been an uptick in vulnerabilities discovered in the software supply chain. An example is the Log4Shell attack in 2021 which allowed attackers to execute arbitrary code on vulnerable servers and affected millions of devices worldwide[8].
The media attention on the Heartbleed bug also revealed that the critical library was maintained by a small team of volunteer coders with only one full-time developer and minimal financial resources to support their work which left the library open to vulnerabilities in the first place[9].
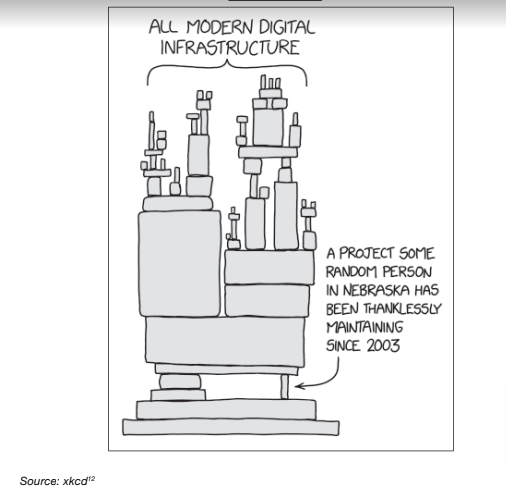
The digital security challenge that the software supply chain faces are not unrelated to the infrastructural challenges and incentives that drive contribution to and adoption of FOSS. Most open-source software is created and maintained by individuals and/or small teams. While almost all software contains open-source software, reports have shown that 94% of OSS projects have fewer than 10 developers writing code[10]. This makes Figure 1 particularly popular in FOSS circles as a succinct description of the problem.
Figure 1: xkcd: Dependency
Another complication is that FOSS varies widely in quality, and open-source software skills are not just “one skill” or “one coding language”. While individuals can contribute to multiple projects, funding one does not mean that other FOSS projects gain any benefits from that funding.
Research has found that FOSS projects are largely unreviewed for security issues, lack adequate systemic safeguards to prevent tampering of code, and do not present users with the tools to verify whether the software they are consuming matches the expected source code[11]. Further, there is no standard way to monitor FOSS components and update them when a vulnerability is discovered. This means that once a vulnerability is identified in a particular library, software developers and security teams will often need to scan through the entire codebases and dependencies to identify and isolate each individual use of a library to be able to update it.
Among technical stakeholders who create software applications, security of the code is often seen as a secondary priority to the expected functionality in day-to-day operations. If a software component has the functionality required, security testing is of lower priority[12]. Further, the use of OSS is often promoted as a cost-cutting exercise and is painted with a consumer attitude which prioritises the ability to quickly resolve problems among companies, and even government policies[13].
There needs to be a recognition that the use of OSS does not mean that the companies and governments get to cut costs in their digital projects, instead, they become part of the broader community that benefits from the continued existence and timely updates of the project chosen. Thus, the key to strengthening security is to strengthen the ecosystem of users and contributors who interact with open-source software.
The Role of G20
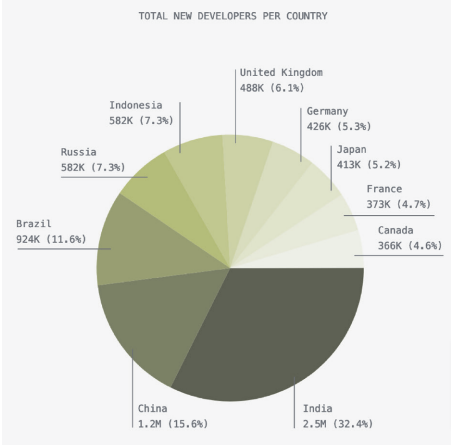
The development and use of FOSS are not restricted by geographic boundaries, making the G20 the ideal venue to take action on securing the software supply chain. Developing and contributing to open source is a global endeavour. Github attracts developers from all over the world with India showing the largest year-over-year increase (32.4%) in developer populations on the platform[14]. Other G20 countries such as Brazil and China are also extremely well represented on the platform[15] (Figure 2).
Figure 2 : The State of Open Source Software, Github
Source: Github18
While not a perfect metric, it can be used to infer open-source software’s global popularity. Since FOSS developers are geographically distributed, problems related to FOSS security also warrant a global response. Global investment in open-source software and its security presents an opportunity to nurture intentional international collaboration.
Recommendations to the G20:
As previously discussed, the supply chain security issues with open-source software (ex. undetected vulnerabilities in widely used libraries) are also the problems facing open source in general (lack of resources and inadequate maintenance). Therefore, to secure the software supply chain for our digital infrastructure, interventions need to be made on two main levels:
- Proactively securing software projects that are critical for everyday operations.
- Developing and sustaining a robust open-source culture and support infrastructure
The sections ahead elaborate on these further. While the recommendations listed are not comprehensive, they are an illustrative starting point towards a more secure software supply chain.
Proactively securing software existing projects
- Identify the most commonly used projects in government and industry. There is an urgent need to identify projects and libraries that are most commonly used and where they are located in the software systems of each company and product[16],[17]. While Github does have some popularity metrics, they are insufficient to identify which FOSS components are in the highest demand. A public-private partnership (or an industry collaboration ex. OpenSFF[18]) is necessary to identify which FOSS projects are the most used across digital products. This must be an internationally collaborative endeavour because the creation and implementation of code is not bound by the geography of the developers.
- Invest in the securing and maintaining of these projects: This list would help governments invest in, support and co-create projects they use most frequently. It would also help projects raise money from external funders towards maintenance costs, server costs etc and recruit team members to critical projects. Support need not only be financial: training resources, upskilling on security best practices, helping projects plan succession workflows once team members move on, and the design and marketing of projects are all ways that can support a small team of FOSS maintainers. There are currently some civil society initiatives like FOSS United[19] and industry initiatives like Github Sponsors[20] that aim to fund FOSS projects, however this funding is currently piecemeal and adhoc.
- Periodic ongoing third-party audits of critical projects are important to identify security issues in the most used FOSS projects so that they can be fixed as common international infrastructure. Some companies perform this function for their clients, and non-profit and industry collaborations like OpenSSF and the Linux Foundation projects like Alpha-Omega[21] are also starting to investigate the larger industry and compile software library level data. An international public-private partnership that periodically audits critical software for vulnerabilities is necessary.
- Communicate identified software vulnerabilities and their fixes: Similar to identifying critical projects, a multistakeholder partnership that keeps track of known software vulnerabilities and communicates fixes to users is necessary[22]. There are government, industry and non-profit bodies that keep track of known software vulnerabilities when they are submitted by volunteers ex. the Common Vulnerabilities and Exposures database[23]. National Computer Emergency Response Teams (CERTs) can play a huge role in communication of software vulnerabilities and their fixes identified through ongoing audits.
- Incentivise the creation and use of a software bill of materials (SBOM) for all public sector projects from vendors. An SBOM keeps track of all dependencies in a digital product so that once a vulnerability is identified in a FOSS component, it can be located and fixed by the upstream users more quickly. Making these a matter of public record would also enable the community to identify and communicate security issues, would help developers streamline the implementation of fixes and get affected systems back online quickly[24].
- Security education for software developers: There is an urgent need to educate developers of FOSS and enterprise software on security best practices like the use of use of memory safe languages for development, fuzz testing projects, securing releases cryptographically, validating existing dependencies and investing in FOSS management tools to ensure secure distribution and loading of FOSS components.[25] Research has shown that delivering a functional product is often the first priority for developers[26]. Given the high stakes with insecure software, security education can ensure that software security does not remain a secondary priority.
Developing and sustaining an open-source culture
Developing and sustaining an open-source culture is an important in ensuring the security of FOSS developed. A review of the literature suggests that there is space for targeted interventions in the following categories which would have cascading effects on the health of the open-source community, and consequently the digital public goods that are created through their efforts[27],[28],[29],[30].
- Government OSS consumption: The government as a large consumer has market-moving and trendsetting potential for FOSS communities.
- Digital policies should focus not only on code usage but also on contribution to the projects used. This can be done by prioritising vendors that contribute to existing projects and co-creating software products with the open-source community directly.
- Procurement policies should mandate that software used for public services should be open-source, not proprietary. If open-source versions are not available, vendors should aim to release infrastructure products under an open-source license so that the entire community may benefit.
- Establish an Open Source Program Office (OSPO) that coordinates the implementation of open source across government departments. This office can be a knowledge centre within the G20 states which can advise on OSS best practices, provide training and aid adoption.
- FOSS contributions from Industry: Incentivising FOSS contributions from technology companies too has the potential to create high-impact, high-quality open-source projects with a dedicated community around them. React[31], a web library for creating user interfaces online, is maintained by Meta and is one of the most popularly used front-end frameworks.
- Education: Curriculums in high schools, colleges and postgraduate institutions should adopt a FOSS-first approach to build FOSS skills in the next generation of software engineers. Education can play a major role in FOSS adoption, by inculcating FOSS values among the next generation of technology creators and keeping developers up to date on the latest security thinking and best practices. FOSS communities in institutes of higher education are a great way for students to be more involved with the larger FOSS community, contribute to existing projects and see the impact of their contributions.
The author thanks Isha Suri, Divyank Katira and Upasana Hembram for their comments and suggestions on this brief.
Endnotes:
[1]“The Open Source Initiative,” Open Source Initiative, Accessed April 4, 2023. https://opensource.org/osd/
[2] “2022 Open Source Security and Risk Analysis Report,” Synopsis, 2022. https://www.synopsys.com/content/dam/synopsys/sig-assets/reports/rep-ossra-2022.pdf.
[3] “2023 Open Source Security and Analysis Report,” Synopsis, 2023. https://www.synopsys.com/software-integrity/resources/analyst-reports/open-source-security-risk-analysis.html.
[4] “The State of Enterprise Open Source: A Red Hat Report,” Red Hat, 2022. https://www.redhat.com/en/resources/state-of-enterprise-open-source-report-2022.
[5] Knut Blind, Sivan Pätsch, Sachico Muto, Mirko Böhm, Torben Schubert, Paula Grzegorzewska, Andrew Katz. 2021. “The impact of open source software and hardware on technological independence, competitiveness and innovation in the EU economy — Final study report,” Publications Office, European Commission, Directorate-General for Communications Networks, Content and Technology. https://data.europa.eu/doi/10.2759/430161
[6] “Report on the 2020 FOSS Contributor Survey,” Linux Foundation, 2022. https://www.linuxfoundation.org/resources/publications/foss-contributor-2020
[7] Joseph Steinberg, “Massive Internet Security Vulnerability — Here’s What You Need To Do.” Forbes, 2014. https://www.forbes.com/sites/josephsteinberg/2014/04/10/massive-internet-security-vulnerability-you-are-at-risk-what-you-need-to-do/?sh=3207221c3fdf
[8] David Uberti, James Rundle, Catherine Stupp, “The Log4j Vulnerability: Millions of Attempts Made Per Hour to Exploit Software Flaw,” The Wall Street Journal, 2021. https://www.wsj.com/articles/what-is-the-log4j-vulnerability-11639446180
[9] Nadia Eghbal, “The Unseen Labor Behind Our Digital Infrastructure.” Ford Foundation, 2016. https://www.fordfoundation.org/work/learning/research-reports/roads-and-bridges-the-unseen-labor-behind-our-digital-infrastructure/
[10] Frank Nagle, James Dana, Jennifer Hoffman, Steven Randazzo, Yanuo Zhou,“Census II of Free and Open Source Software — Application Libraries” The Linux Foundation and The Laboratory for Innovation Science at Harvard, 2022. https://www.linuxfoundation.org/research/census-ii-of-free-and-open-source-software-application-libraries
[11] Divyank Katira, “Securing Our Dependence on Code Reuse in Software.” Centre for Internet and Society, April 2023. https://cis-india.org/openness/securing-our-dependence-on-code-reuse-in-software
[12] Divyansha Sehgal, “Security of Open Source Software: A Survey of Technical Stakeholders’ Perceptions and Actions,” Centre for Internet and Society, April 2023. https://cis-india.org/openness/security-of-open-source-software-a-survey-of-technical-stakeholders2019-perceptions-and-actions-1
[13] Apar Gupta, “Analysis of FOSS Government Policies in India,” 2022. http://dx.doi.org/10.2139/ssrn.4146240
[14] “The State of the Octoverse,” Github, 2022. https://octoverse.github.com/2022/global-tech-talent.
[15] Github, “The State of the Octoverse.”
[16] Divyank Katira, “Securing Our Dependence on Code Reuse in Software.”
[17] “The Open Source Software Security Mobilization Plan.” Whitepaper. OpenSSF, and The Linux Foundation, 2022. https://openssf.org/oss-security-mobilization-plan/.
[18] “Open Source Security Foundation (OpenSSF),” OpenSSF, accessed March 24, 2023. https://openssf.org/.
[19] “Funding and Grants,” FOSS United, accessed Jun 15, 2023. https://fossunited.org/grants.
[20] “Github Sponsors : Invest in software that powers your world,” Github, accessed Jun 15, 2023, https://github.com/sponsors.
[21] “Alpha-Omega,” OpenSSF, accessed Jun 15, 2023. https://openssf.org/community/alpha-omega/
[22] OpenSSF and The Linux Foundation, “The Open Source Software Security Mobilization Plan.”
[23] “Overview,” Common Vulnerabilities and Exposures, accessed Jun 15, 2023. https://www.cve.org/About/Overview
[24]Amelie Koran, Wendy Nather, Stewart Scott, and Sara Ann Brackett. “The Cases for Using the SBOMs We Build.” The Atlantic Council, 2022. https://www.atlanticcouncil.org/in-depth-research-reports/issue-brief/the-cases-for-using-sboms/.
[25] Divyank Katira, “Securing Our Dependence on Code Reuse in Software.”
[26] Divyansha Sehgal, “Security of Open Source Software: A Survey of Technical Stakeholders’ Perceptions and Actions.”
[27] “The State of Free and Open Source Software in India,” CivicDataLab, 2022. https://state-of-foss.in/the-state-of-foss-report.pdf.
[28] Nadia Eghbal, “The Unseen Labor Behind Our Digital Infrastructure.”
[29] Apar Gupta Arjun Gargeyas, Bharat Reddy, Kailash Nadh, Nitin Pai, Pranay Kotasthane, Rushubh Mehta, Saurabh Chandra, and Venkatesh Hariharan. 2023. “An Open Tech Strategy for India.Version 1.2.” Takshashila Institution. https://takshashila.org.in/research/an-open-tech-strategy-for-india
[30] Stewart Scott, Sara Ann Brackett, Trey Herr, and Maia Hamin, “Avoiding the Success Trap: Toward Policy for Open-Source Software as Infrastructure,” The Atlantic Council, 2023. https://www.atlanticcouncil.org/in-depth-research-reports/report/open-source-software-as-infrastructure/.
[31] “React,” React, Meta Open Source, accessed March 24, 2023. https://react.dev/